- Use Stack Protector All (stack Canaries For Macs
- Use Stack Protector All (stack Canaries For Macbook Pro
Use Stack Protector All (stack Canaries For Macs

- I am able to produce a binary with Clang that has either a stack canary or SafeStack protection, but not both. SafeStack seems to take precedence if both the '-fstack-protector-all' and '-fsanitize=safe-stack' options are specified. Are these Clang options mutually exclusive? I cannot seem to find anything elsewhere pertaining to this issue.
- Download Op.gg For League Of Legends For Mac Mac Os X 10.3 Panther Dmg Download Tomcat 8 For Mac Reg-cleaner For Mac Aescripts Plugins Collection For Mac Finale Mac Os Sierra Torrent How To Add Cell Dropdown In 2011 Excel For Mac Download Processing 1.5 For Mac Use Fstack-protector-all (stack Canaries For Mac Contact.
- Implement stack-smashing protection - Compile the application with the -fstack-protector-all compiler flag to protect your application against buffer overflow attacks.
Fstack-protector-all: This is same as -fstack-protector, but applied to all function rather than just vulnerable functions.-fstack-protector-strong: -fstack-protector is available only for functions with character arrays & -fstack-protector-all is an overkill for performance.fstack-protetion-strong extend this protective mechanism to functions with any type of arrays & length: structs. With –fstack-protector-all I’m instrumenting all functions. Of course that instrumentation has a cost a runtime. Of course that instrumentation has a cost a runtime. The other thing is that the startup code might cause false alarm if the canary variable has not been setup yet or is not initialized yet.
I have a few questions about Stack Guard and SSP protections. First question is about Stack Guard and its three types of canaries, if I am correctly - terminator, random and random XOR.
1) I'd like to know, how to disabled Stack Guard on x86 Linux system? Somewhere I read, it's possible with this command, while compiling with gcc '-disable-stackguard-randomization', it's same like with this command for enable '-enable-stackguard-randomization', both doesn't work. If needed, my gcc version is 4.8.2.



2) Next question about Stack guard, when I will able to enable/disable it, how can I set, which type of canaries I want to use? What I read, terminator canaries are used by default, for random I have to compiled with '-enable-stackguard-randomization', but how about random XOR? (Or with null 0x00000000)
3) Now about SSP(ProPolice), I know, for random canary I have to compiled with 'fstack-protector-all', but how about terminator, is it same as in Stack Guard, by default?
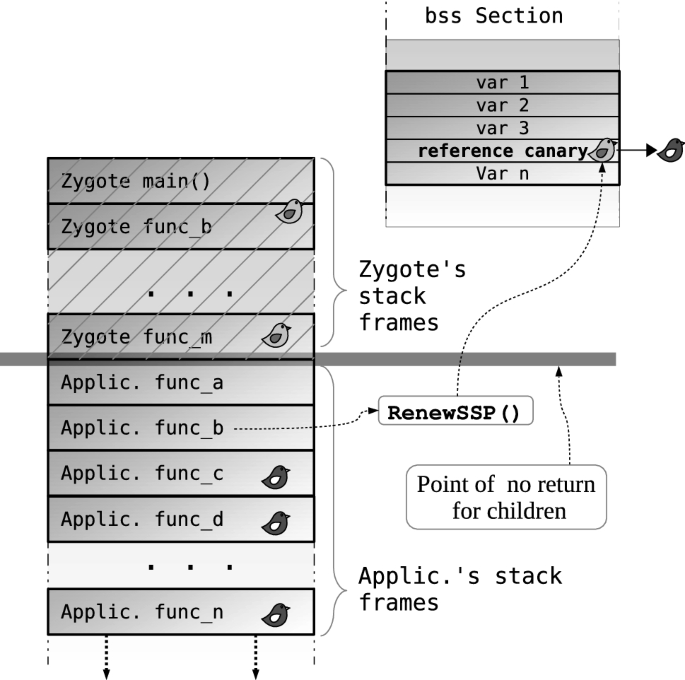
4) Last one, if anyone of you, can tell me, where I can find random canary in memory. For example, I have this scenario - compiled C program, like 'gcc -g example.c -o example -fstack-protector-all', so with random canaries. Let's say, I'm able to get address of canary, after every execution. So expect, I have: Canary = 0x1ae3f900. From a different papers, I get some info, that canary is located in .bss segment. So I get address of .bss segment using readelf: 'readelf -a ./example | grep bss'. It's 080456c9. In gdb I set some breakpoints, to get address of canary, but when I check .bss address x/20x 0x080456c9, all I see are only 0x00000000 addresses, butcanary is nowhere. Plus, I checked __stack_chk_fail's if it isn't there, but with same result, I can't see it there. I get address of stack_chk_fail from PLT/GOT.
- I am able to produce a binary with Clang that has either a stack canary or SafeStack protection, but not both. SafeStack seems to take precedence if both the '-fstack-protector-all' and '-fsanitize=safe-stack' options are specified. Are these Clang options mutually exclusive? I cannot seem to find anything elsewhere pertaining to this issue.
- Download Op.gg For League Of Legends For Mac Mac Os X 10.3 Panther Dmg Download Tomcat 8 For Mac Reg-cleaner For Mac Aescripts Plugins Collection For Mac Finale Mac Os Sierra Torrent How To Add Cell Dropdown In 2011 Excel For Mac Download Processing 1.5 For Mac Use Fstack-protector-all (stack Canaries For Mac Contact.
- Implement stack-smashing protection - Compile the application with the -fstack-protector-all compiler flag to protect your application against buffer overflow attacks.
Fstack-protector-all: This is same as -fstack-protector, but applied to all function rather than just vulnerable functions.-fstack-protector-strong: -fstack-protector is available only for functions with character arrays & -fstack-protector-all is an overkill for performance.fstack-protetion-strong extend this protective mechanism to functions with any type of arrays & length: structs. With –fstack-protector-all I’m instrumenting all functions. Of course that instrumentation has a cost a runtime. Of course that instrumentation has a cost a runtime. The other thing is that the startup code might cause false alarm if the canary variable has not been setup yet or is not initialized yet.
I have a few questions about Stack Guard and SSP protections. First question is about Stack Guard and its three types of canaries, if I am correctly - terminator, random and random XOR.
1) I'd like to know, how to disabled Stack Guard on x86 Linux system? Somewhere I read, it's possible with this command, while compiling with gcc '-disable-stackguard-randomization', it's same like with this command for enable '-enable-stackguard-randomization', both doesn't work. If needed, my gcc version is 4.8.2.
2) Next question about Stack guard, when I will able to enable/disable it, how can I set, which type of canaries I want to use? What I read, terminator canaries are used by default, for random I have to compiled with '-enable-stackguard-randomization', but how about random XOR? (Or with null 0x00000000)
3) Now about SSP(ProPolice), I know, for random canary I have to compiled with 'fstack-protector-all', but how about terminator, is it same as in Stack Guard, by default?
4) Last one, if anyone of you, can tell me, where I can find random canary in memory. For example, I have this scenario - compiled C program, like 'gcc -g example.c -o example -fstack-protector-all', so with random canaries. Let's say, I'm able to get address of canary, after every execution. So expect, I have: Canary = 0x1ae3f900. From a different papers, I get some info, that canary is located in .bss segment. So I get address of .bss segment using readelf: 'readelf -a ./example | grep bss'. It's 080456c9. In gdb I set some breakpoints, to get address of canary, but when I check .bss address x/20x 0x080456c9, all I see are only 0x00000000 addresses, butcanary is nowhere. Plus, I checked __stack_chk_fail's if it isn't there, but with same result, I can't see it there. I get address of stack_chk_fail from PLT/GOT.
Thank in advance for your answer and time.
